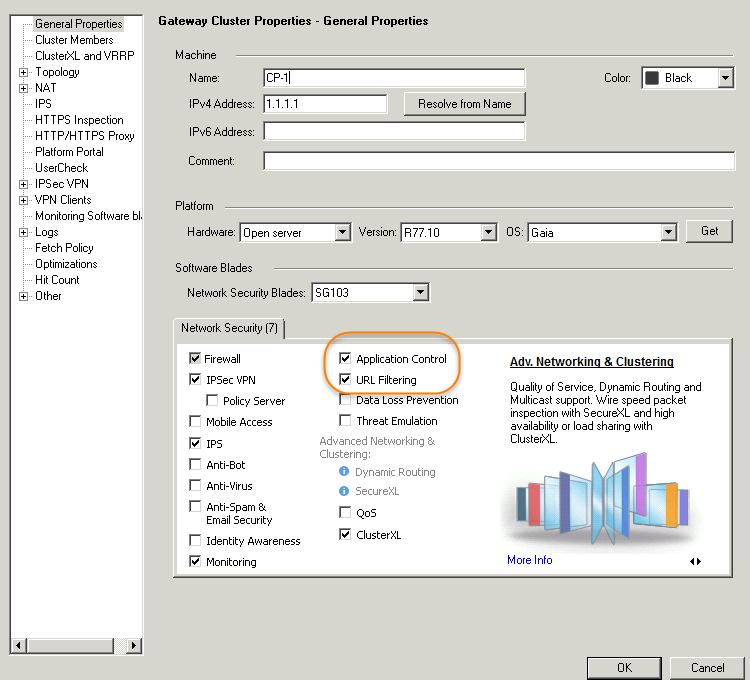
Three Steps to Enable Checkpoint Firewall Application Control and URL Filtering – CyberSecurity Memo
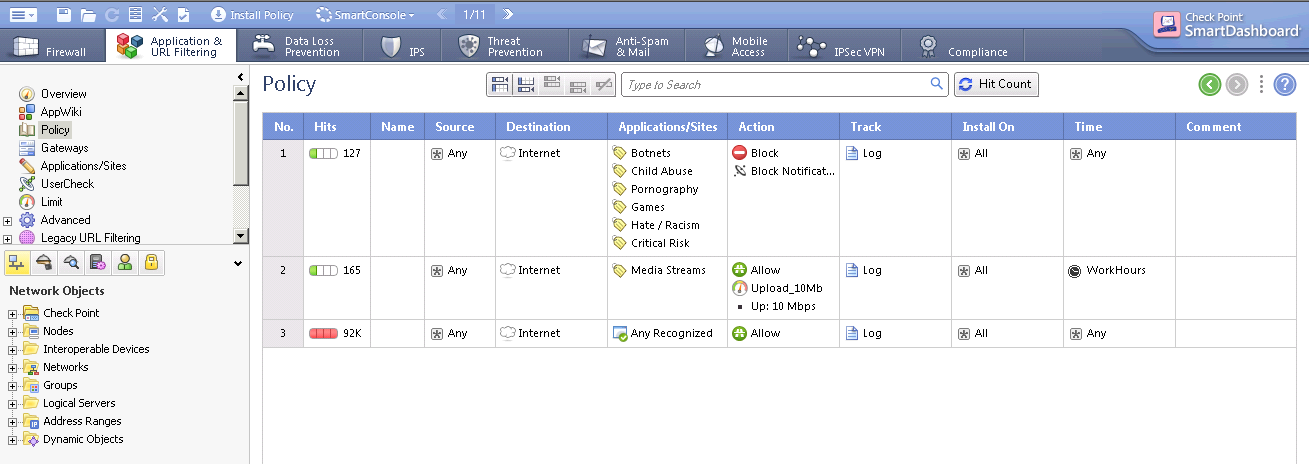
Three Steps to Enable Checkpoint Firewall Application Control and URL Filtering – CyberSecurity Memo
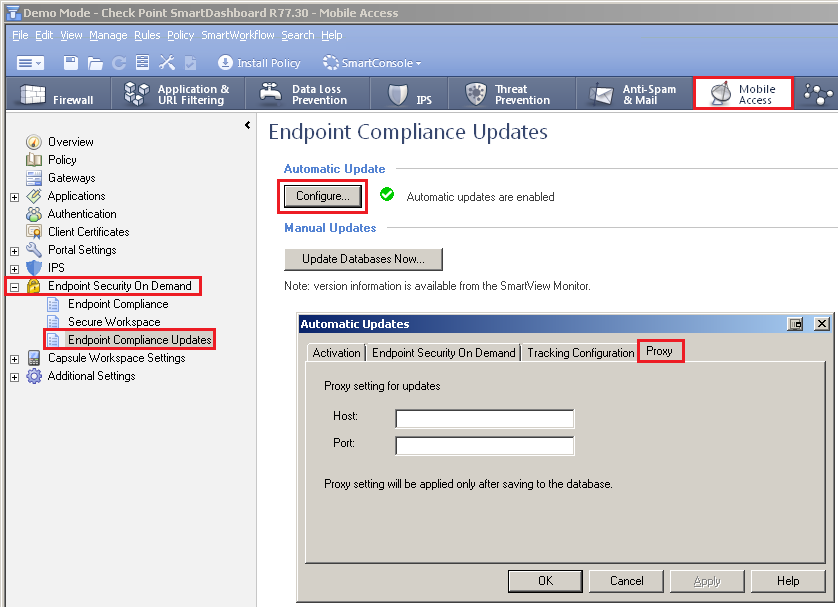
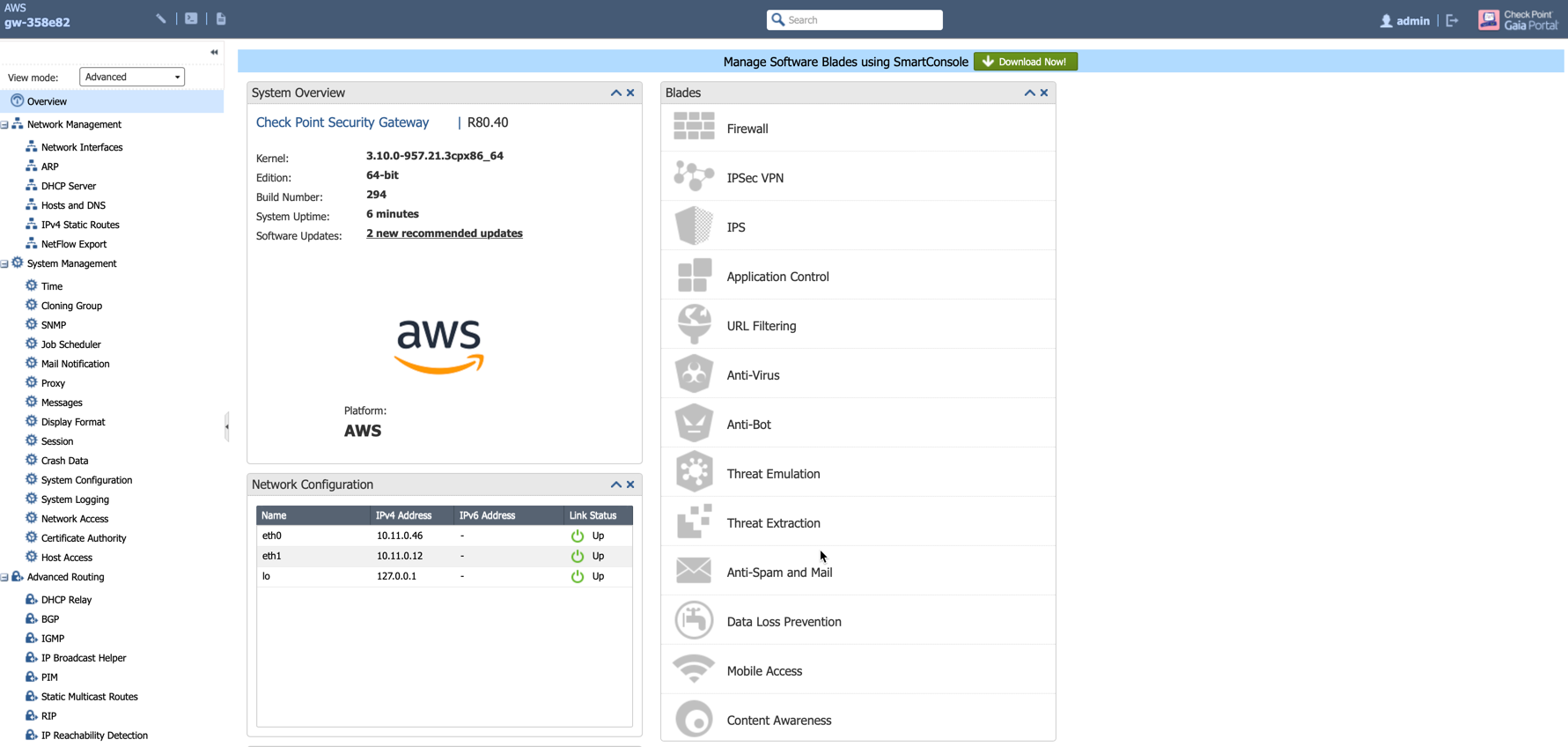
How to verify that Security Gateway and/or Security Management Server can access Check Point servers?
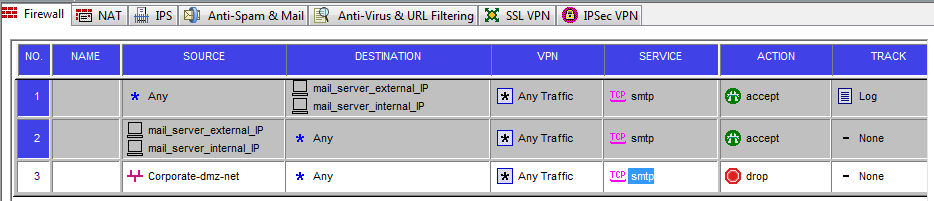










![PDF] Mastering spam: a multifaceted approach with the Spamato spam filter system | Semantic Scholar PDF] Mastering spam: a multifaceted approach with the Spamato spam filter system | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/231a588037f86948967e1ece659629ac1279373d/23-Figure2.4-1.png)